In an era increasingly dominated by digital communication, the specter of cybersecurity breaches looms ever larger. Amidst the plethora of encryption methods available, quantum cryptography emerges as a particularly alluring beacon of security. Yet, one must ponder a critical question: Is quantum cryptography truly unbreakable? This query invites us to engage with both the theoretical underpinnings and practical implications of quantum cryptography while examining the very definition of “unbreakable.”
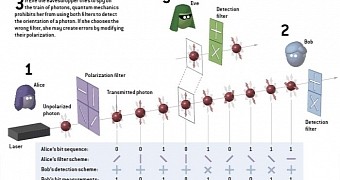
At its core, quantum cryptography leverages the principles of quantum mechanics to establish a communication channel that is purportedly impervious to eavesdropping. The most notable implementation is Quantum Key Distribution (QKD), where twin particles—often photons—are employed to securely generate and share encryption keys between communicating parties. The groundbreaking aspect lies in the phenomenon known as “quantum superposition,” which allows a photon to exist in multiple states simultaneously, facilitating the creation of secure keys.
However, the essence of quantum cryptography’s allure extends beyond mere theory; it hinges on a critical principle known as the “No-Cloning Theorem.” This theorem posits that it is impossible to create an identical copy of an arbitrary unknown quantum state. Thus, any attempt by an eavesdropper, dubbed “Eve”, to illicitly intercept the communication would inherently disturb the quantum state of the particles being observed, thus alerting the legitimate parties—typically referred to as “Alice” and “Bob”—to the interception.
But does this mean quantum cryptography stands as an unassailable fortress in the realm of cybersecurity? As we delve deeper into this issue, playful curiosity emerges: might there be chinks in this quantum armor? For instance, while the initial premise of QKD is robust, it is often contingent upon the practical implementation of the technology. The sophisticated nature of quantum systems introduces real-world challenges, including flaws in the hardware and software or environmental interference that could undermine the theoretical guarantees of security.
That leads us to the paramount challenge of scalability. The current infrastructure needed for widespread quantum cryptography deployment is not completely developed. Quantum key distribution systems require specialized equipment such as single-photon sources, quantum repeaters, and celestial-grade detection methods, all of which can present substantial cost and logistical challenges. Therefore, while quantum cryptography presents an impressive theoretical framework, the practicality of its implementation raises valid concerns regarding its universality and feasibility in everyday applications.
Moreover, the concept of “unbreakable” assumes that all potential attacks are countered successfully. However, as the field of computer science progresses, especially with advances in quantum computing itself, the horizon of potential threats expands. Quantum computers may hold the capability to solve certain problems far more efficiently than classical counterparts, posing a challenge to classical encryption methods. Yet they threaten quantum cryptography in an indirect manner—by enabling more sophisticated algorithms that could potentially find weaknesses in its practical implementation.
It is crucial to address another layer of complexity: the human element. Even the most fortified systems can be compromised through social engineering or human error. Phishing attacks, for instance, could deceive Alice or Bob into disclosing their cryptographic keys, thereby nullifying the quantum system’s advantages. Thus, while the quantum technology itself may hold promise, the human factors surrounding its use must not be underestimated.
Additionally, one must consider the legal and ethical implications entangled with quantum cryptography. As governments and corporations race to advance their cryptographic capabilities, questions arise regarding regulation, privacy, and state surveillance. The potential misuse of quantum technologies, coupled with the ongoing debate over cryptographic backdoors, introduces an ethical dilemma: how do we balance the need for secure communication with the need for oversight? This socio-political complexity challenges the simplistic notion of quantum cryptography as a straightforward solution to our security dilemmas.
Nevertheless, within this landscape of uncertainty, there exist promising avenues of research that may enhance the security of quantum communication systems. For instance, advancements in entanglement-based QKD have been shown to provide even greater resistance to eavesdropping, thus pushing the boundaries of what can be achieved within the quantum realm. These breakthroughs signify that while quantum cryptography might not yet be unbreakable, it could evolve into an increasingly resilient technology, increasingly refined by emerging research.
In conclusion, quantum cryptography presents an intriguing proposition: a method of secure communication rooted in the fundamentals of quantum mechanics. While it stands as a powerful alternative to classical encryption techniques, labeling quantum cryptography as unbreakable is somewhat presumptive. The interplay of physical principles, technological constraints, and human factors means that its practical durability remains an open question. As we navigate through the uncharted waters of quantum technology, it is essential to remain vigilant, ever-aware that with each new advancement lies an equal opportunity for challenge. Thus, as we ponder the extent of quantum cryptography’s security, we are reminded that in science, the inquiries often open a Pandora’s box of further exploration and deeper understanding.